Android- The powerful, versatile and flexible Mobile OS from Google is rocking and will surpass other OS shortly. Unfortunately now Android is the pet OS of malware coders. Since the mobile handsets carry your identity, these threats are much dangerous than the infections in normal computers. Heart of Android OS is Linux, which is one of the robust operation system and almost free from the malware and virus infections, then what makes Android odd? None of the applications can intrude into your Android phone without your permission. Here the word “Permission” is very much important. Knowingly or unknowingly users fall into the trap of the malicious applications and they steal the administrative privileges smartly.
Countless Android applications are available in market for download free as well as paid. Competition in Android application market is also very high. Google revealed that up to 260,000 people had downloaded 58 malicious apps from various sources. Android application marketplace is open and Google is not enforcing strict verifications or authentications on applications. However after the recent disaster Google has remotely wiped out these malicious applications through the Kill Switch feature.
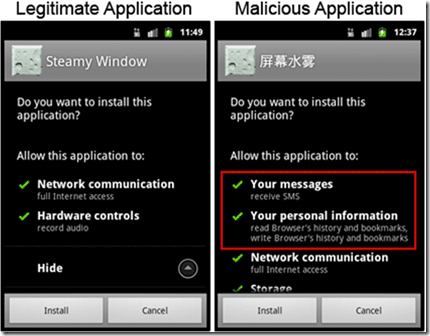
Understand the Application permissions
Each and every Android Application runs with a distinct identity. The permission mechanism in Android OS enforces restrictions on particular operation that a process can run.
By default none of the applications are permitted to do operations that would adversely affect other applications, user experience or operating system.
For each and every Android application there must be some permissions required for installation. The system prompts users to grant permission during the application installation process. Permissions are not given dynamically. You must be very much clear about what these permission stands for. For example you are installing a Simple Snake Game. During the installation process if that application demands GPS usage, Internet access, SMS access etc. then you can smell the danger . Don’t do the installation in hurry. Thoroughly analyze installation steps and read all the warnings and permission requests.
Never do “Always Allow” permission if you are not sure about that
Some applications asks “Always Allow” permissions for SMS, Internet, GPS, Contact access. Never grant “Always allow” permission to the application if you are not sure what it warrants . Even it is very difficult to analyze the exact demand of application, it’s important to use the applications from trusted developers.
Use the applications of trusted developers and firms
To stay away from the potential malware attack, always download the applications of reputed developers. Don’t download and install the applications only reading the user reviews, comments etc. These can be manipulated. Some malicious applications show their original color immediately after the installation once they get enough reputation and widespread popularity, then will start working. Set your phone’s Application settings to deny Non Market Applications. Remember Android Market applications are also not 100% risk free.
Don’t use pirated applications
Don’t be attracted towards the free versions of popular Android applications and Games. Never download and install the cracked applications from file sharing sites
RELATED POSTS
View all